We intercepted this communication on the internal network and we made a pivoting to the administration page of a spy cell, but we do not have a wifi password to decode and access a page of them. Can you help us?
Tip: I think they use a custom password with shx.
Solution
On this challenge we have access to a router administration page..
and a pcap file..
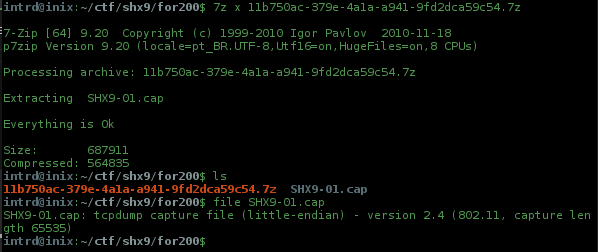
I've bruteforced this router admin page w/ some common logins/passwords, but no success..
If we load this .pcap at Wireshark, all 802.11 traffic is encrypted.. so we need to crack this password and decrypt w/ master key.
Used aircrack-ng extracting the hash to work with Hashcat (with Hashcat my GPU performs better than John and Pyrit)
aircrack-ng SHX9-01.cap -J shx9
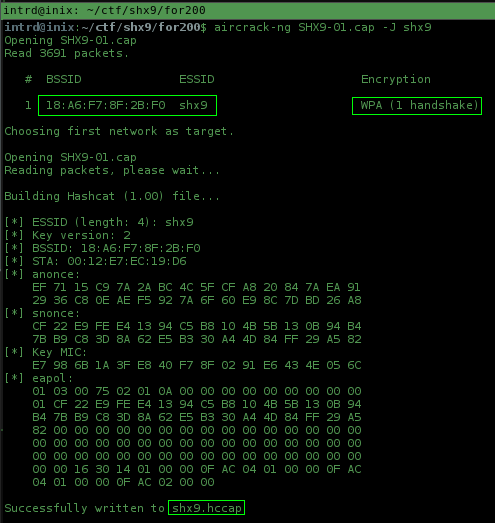
Update: If you have problem with hccap version, use this: https://hashcat.net/cap2hccapx/ to generate a hccapx. (thx dbaser)
As you can see, it's a WPA-PSK, challenge description give a tip, we need to generate a wordlist containing "shx" at permutations.
So, WPA-PSK starts w/ lentgh = 8, and I do not believe that shellterlabs used a password above 8~9 digits because it would consume a lot of processing power to crack.
Then, my 1st permutation started w/ shx?1?1?1?1?1, every ?1 contains ?l?d?s, all lower letters, simbols and digits. Hashcat is awesome, because we can do this permutations on the fly..
/home/intrd/appz/hashcat/hashcat64.bin -m 2500 shx9.hccap -a3 -1 ?l?d?s shx?1?1?1?1?1
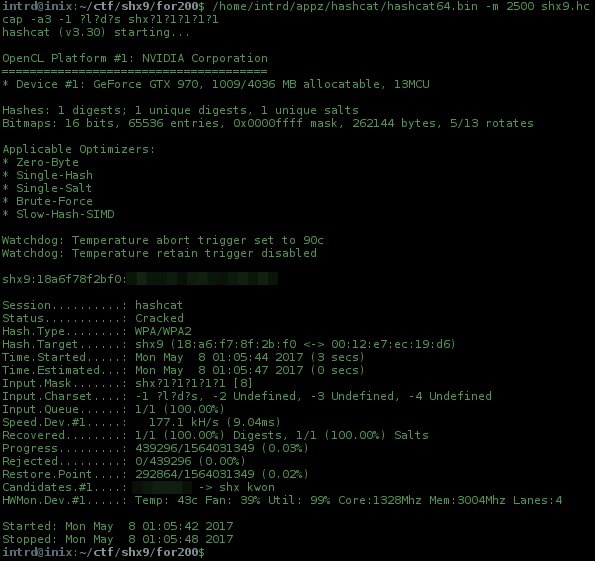
Nice! Recovered the password on my first try! If won't worked i'll try ?1?1?1?1?1shx and soon, crunch can help u w/ more advanced permutations.
Wireshark needs WPA-PSK Master Key to decrypt traffic and hashcat didn't give to us..
Knowing the plain text password is easy to get the Master Key doing this:
echo "sample@p@ssword" >> pwds
echo "sample@p@ssword" >> pwds
echo "sample@p@ssword" >> pwds
aircrack-ng -b 18:A6:F7:8F:2B:F0 -w pwds SHX9-01.cap
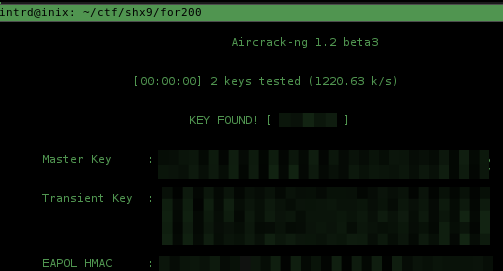
With the master key, launch Wireshark and decrypt all 802.11 traffic between client and router.
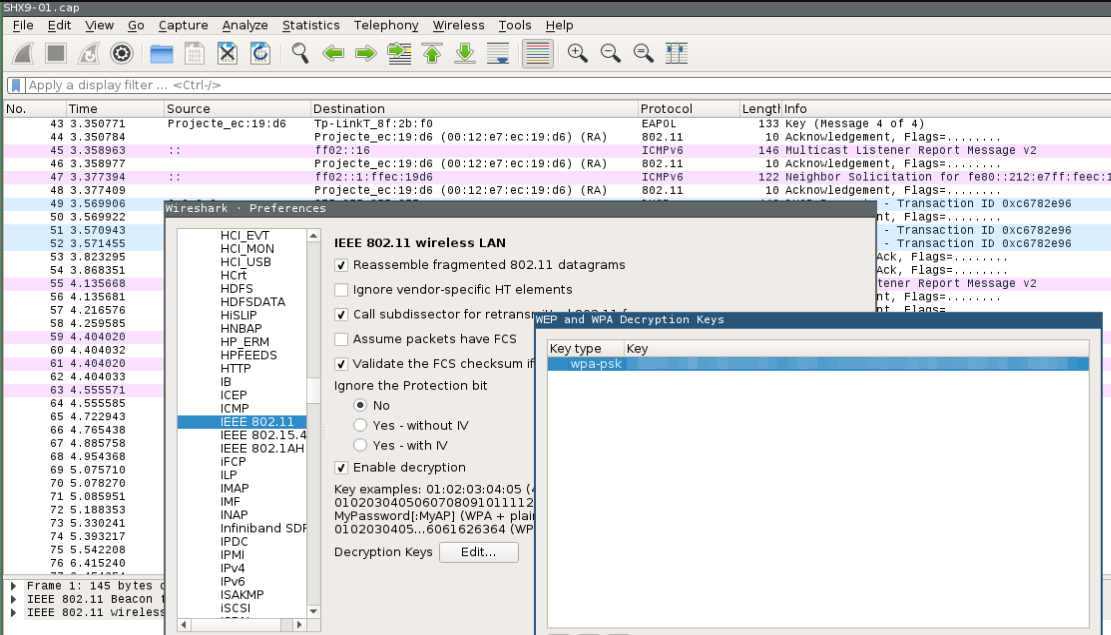
Update: You can decrypt traffic without the need of wireshark airdecap-ng -e shx9 -p sample@p@ssword SHX9-01.cap, thx marcioRAGarcia )
And now, follow all the GET/POST requests between router and client and you will find the HTTP basic auth coded in base64 w/ our admin page login/password!
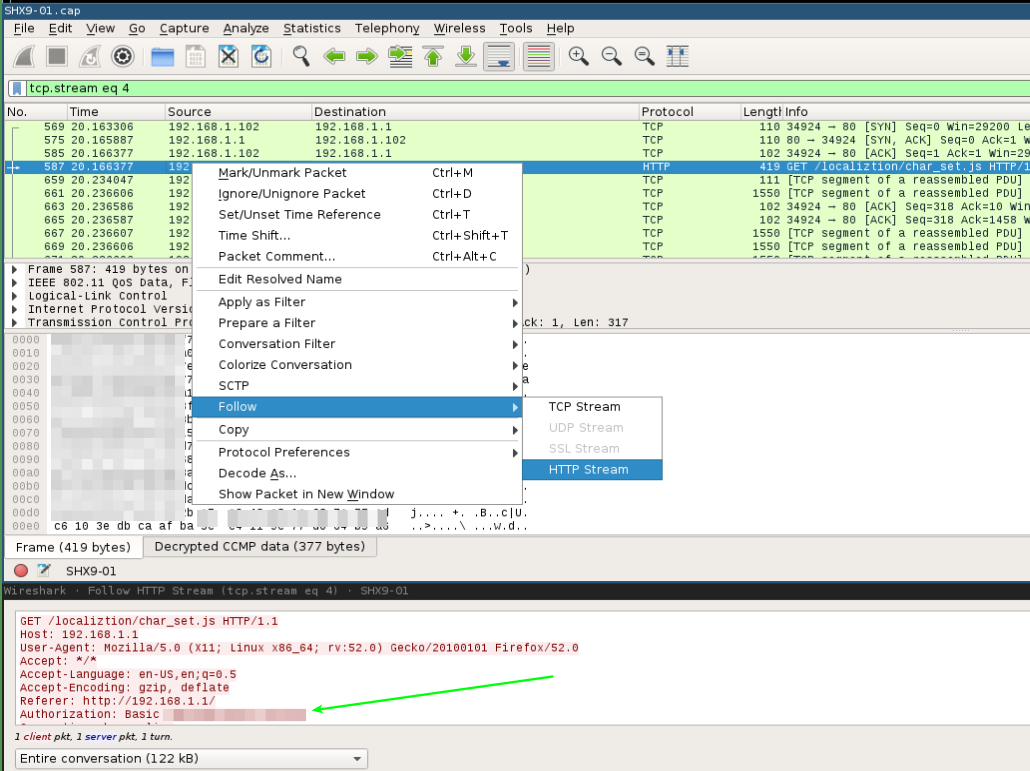
echo captured_http_basicauth | base64 --decode
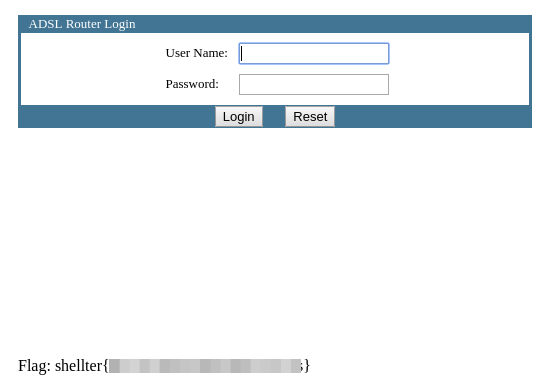
Router pwned, client pwned!
..and there is our flag!
References
- Hashcat wiki - https://hashcat.net/wiki/
- How to Crack WPA/WPA2 - https://www.aircrack-ng.org/doku.php?id=cracking_wpa
 intrd has spoken
intrd has spoken