Find the flag inside the binary.
Flag format: "3DS{flag}"
Solution
Received a file rev1.rar w/ a binary(rev1_merces) ELF 32bit
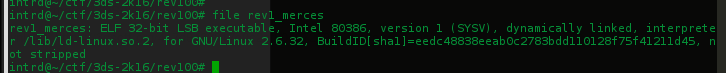
Strings returned something..
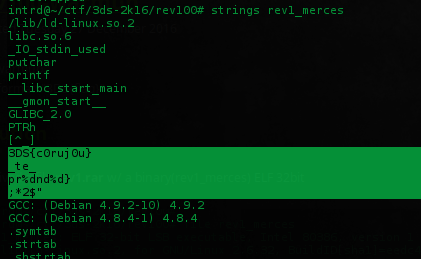
Tried this fake flag and some combinations: 3DS{c0ruj0u}, 3DS{c0ruj0u_te_prende}.. no success.
Launched radare2 and look for the functions..
$ radare2 -Ad rev1_merces
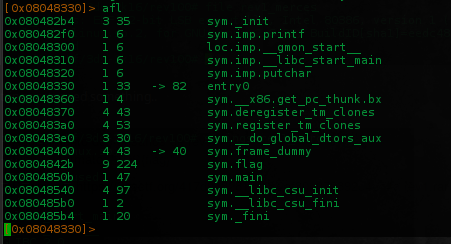
We can see two interesting functions main(), flag() and the eip does not point to main() by default, maybe need some args..
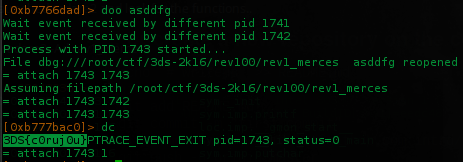
With some args it runs main() and displays the fake flag.. so lets take a look inside flag() function
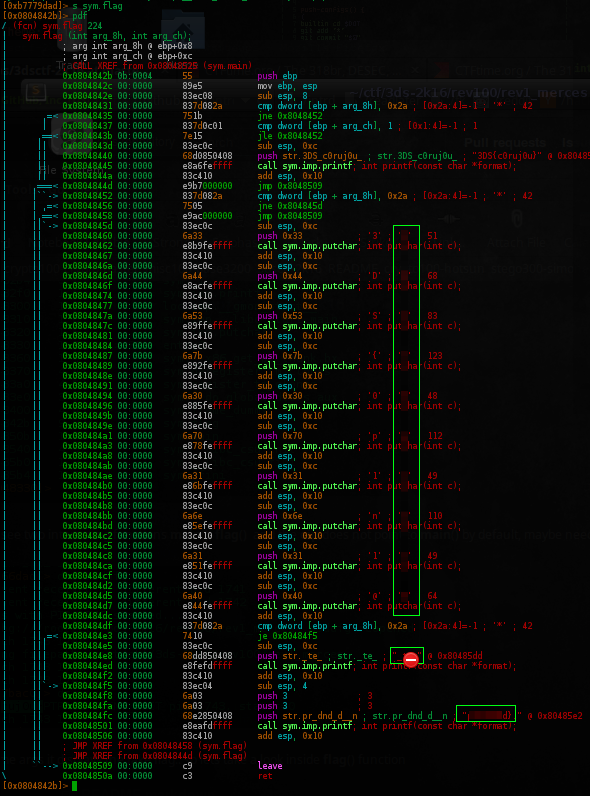
As u can see, its already possible to figure out the flag.
This functions gets the fake flag and add/remove chars, do a lot of shit and return the true flag..
Ok, i've set a breakpoint at entry point 0x08048330 and start doing some jumps reading the esp data..
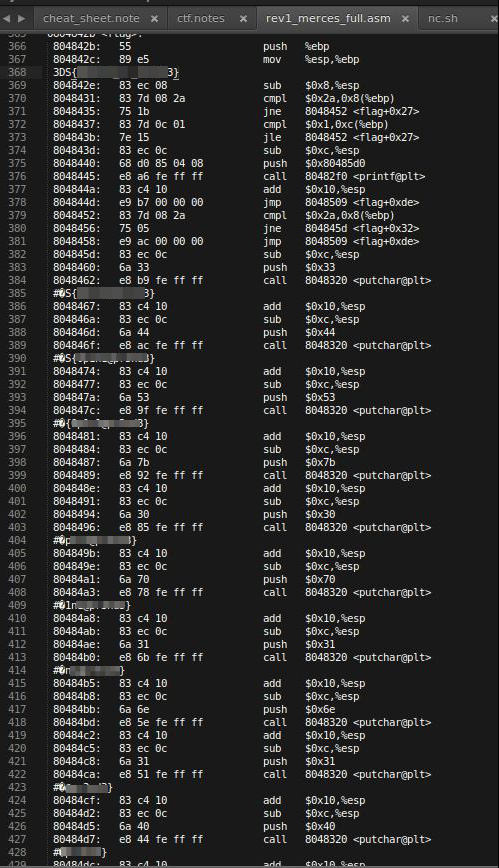
The last one is 0x804842b, who returned the full flag.
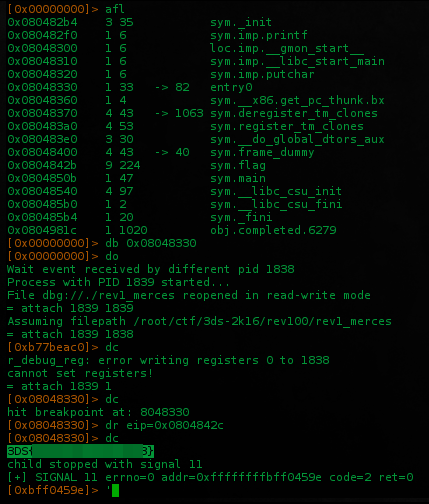
Jumping to the beginning of flag() function 0x804842b didn't returned the flag.. we need to jump to 0x804842c
Maybe this function generate the full flag break it again then return..
Patching the binary to always return the flag
Start radare in debug+write mode
$ radare2 -Adw rev1_merces
go to entry point and rewrite it w/ a jmp to that address who return the flag..
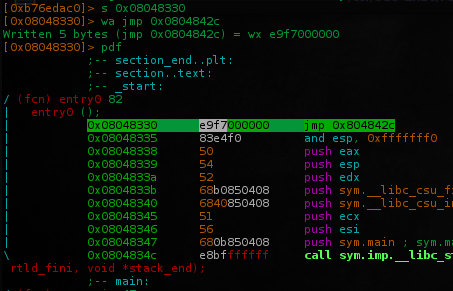
get out the radare and run the patched program..
All done.
Flag: 3DS{CENSORED}
 intrd has spoken
intrd has spoken